Nowadays, cyber-attacks and cyber-crime in different variations are just daily events that need to be defended against. In today’s age of sophisticated digital hackers and cyber criminals, your concern shouldn’t be about if you’re going to get hacked, but what you’re going to do when it happens.
Large companies hit by cyber-crime have made headlines in 2017, and 2018 will have its own share of high-profile breaches. As the threat landscape continues to evolve, cybercriminals are becoming more creative in expanding their attack vectors. Industries spend billions trying to prevent every imaginable threat, but experts tell you that, no matter how much you spend, it’s never enough as security doesn’t rely on prevention alone.
But, what do you need?
Security professionals say, to survive cyberattacks, the most effective way to coordinate your defenses, is with a Security Operations Center (SOC).
What is it? A Security Operations Center is an organized facility to continuously monitor and improve an organization’s security posture while preventing, detecting, analyzing, and responding to cyber security incidents with the aid of both technology and well-defined processes and procedures.
With SOC, the organization gets an opportunity to uncover all of the major network susceptibilities and weaknesses and can form the heart of effective detection. It can enable information security functions to respond faster, work more collaboratively and share knowledge more effectively.
SOC’s main task is responsible for reporting every threat and handle indications that something is wrong in the network or system and stop them quickly.
What do we need to have an effective SOC?
Well, we think it’s better to have it classified into different phases:

PREVENT & PROTECT
Our first layer of defense-prevent intruders, protect the network.
Cyber Security Training Awareness
 No matter how you protect your valuable assets, it will still be useless if your personnel do not know or understand how to maintain confidentiality of information, or how to secure it appropriately.
No matter how you protect your valuable assets, it will still be useless if your personnel do not know or understand how to maintain confidentiality of information, or how to secure it appropriately.
The human factor is a major aspect of protecting your business. Human behavior can make or break a hacker’s attempt at exploiting company information.
Employees should receive information about who to contact if they discover a security threat instead of handling it on their own and be taught that data is a valuable corporate asset. Help them to recognize the threats and vulnerabilities to their company’s information assets and respond to them appropriately including detailing the countermeasures that can be adopted.
Next-generation Firewalls
 Traditional firewalls aren’t intelligent enough to distinguish different kinds of web traffic. Protection based on ports, protocols, IP addresses are no longer feasible. Businesses needs a more robust form of security that wasn’t just tied to the IP addresses.
Traditional firewalls aren’t intelligent enough to distinguish different kinds of web traffic. Protection based on ports, protocols, IP addresses are no longer feasible. Businesses needs a more robust form of security that wasn’t just tied to the IP addresses.
Next-generation firewalls also include integrated intrusion detection systems (IDS) and intrusion protection systems (IPS) that detect attacks based on traffic behavioral analysis, threat signatures or anomalous activity. Next-generation firewall devices monitor traffic intelligently to determine what exactly is being sent or received and includes antivirus and malware protection that’s continuously upgraded automatically whenever new threats are discovered.
But before you decide to purchase a firewall for your protection, you need to see and check what best suits your organization. To help you choose, DCT offers free Proof of Concept that lets you use our network appliances for free to better understand your requirements!
File Security
Companies face the monumental challenge of establishing strong and persistent data protection to ensure files containing sensitive, regulated and confidential information remain protected. The challenge is how to fortify defenses across file sharing mechanisms and infrastructure while optimizing user productivity and business collaboration.
The FinalCode File Security Platform provides organizations with an easy, comprehensive and persistent means to protect sensitive files within and outside the corporate network – even after the files may become further exposed due to: inappropriate or unsanctioned collaboration, unauthorized network folder access, inadvertent email, lost or serviced devices, and removal of files from cloud- and container-based applications.
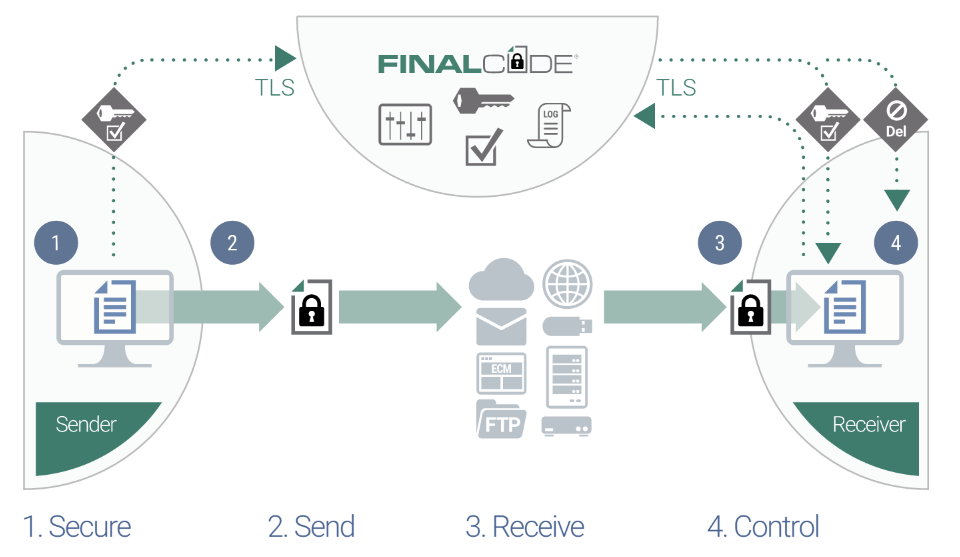
With FinalCode, your employees can share confidential files internally and externally with confidence, knowing that unauthorized recipients will not have access. All file access and usage, both authorized and unauthorized, is logged and available to the file owner and enterprise. The entire system is designed for automated onboarding for file owners and for both internal and external recipients.
IDENTIFY
After you have placed a reliable first level of defense, maybe it’s time to look at your cybersecurity posture.
Penetration Test or Pen Testing
 Understanding who you are defending against and how they will attack you is crucial. Penetration Test will give you the insight to see where the flaws are in your cyber security posture and highlight the problem.
Understanding who you are defending against and how they will attack you is crucial. Penetration Test will give you the insight to see where the flaws are in your cyber security posture and highlight the problem.
The purpose of a penetration test is to identify key weaknesses in your systems and applications, to determine how to best allocate resource to improve the security of your application, or organization as a whole.
DETECT
Here lies the heart of our effective Security Operations Center. After all, our main purpose is to detect threats before it even executes.
Logs and Event Management (LEM)
SOCs typically are based around the underlying principles of every SIEM system, to aggregate relevant data from multiple sources, web site assessment and monitoring systems, application and database scanners and take appropriate action.
For example, when a potential issue is detected, a LEM logs additional information, generate an alert and instruct other security controls to stop an activity’s progress together with the correct integration with our first level defenses.

Get track of your network status and prevent threats altogether with Solarwinds Log and Event Manager.
RESPOND
Sophos Intercept X
 Your goal is now to prevent threats from reaching your devices, stop them before they run, detect them if they have bypassed preventative methods, and not just clean up malware, but analyze and undo everything it does to your endpoints. CryptoGuard technology detects spontaneous malicious data encryption to stop ransomware in its tracks. Identifying malware and isolating and removing it solves the immediate problem.
Your goal is now to prevent threats from reaching your devices, stop them before they run, detect them if they have bypassed preventative methods, and not just clean up malware, but analyze and undo everything it does to your endpoints. CryptoGuard technology detects spontaneous malicious data encryption to stop ransomware in its tracks. Identifying malware and isolating and removing it solves the immediate problem.
Sophos Intercept X compliments existing anti-malware and antivirus implementations delivering powerful next-gen anti-exploit and anti-ransomware protection traditional products lack.
By eliminating the attack vectors which traditional solutions don’t block, Sophos Intercept X helps to harden your security posture and increase resilience.
RECOVER
Backup and Recover
Backups are typically performed on a daily basis to ensure necessary data retention. Disaster recovery requires a separate production environment where the data can live. Backups are useful for immediate access in the event of the need to restore a document. The overall benefits and importance of a disaster recovery plan are to mitigate risk and downtime, maintain compliance and avoid outages.
 Partnering with Veeam, DCT provides Backup and Disaster Recovery Services catered for your needs.
Partnering with Veeam, DCT provides Backup and Disaster Recovery Services catered for your needs.
Active Protection
 It has been said that the ultimate ransomware countermeasure is backup. Cloud based data backup solutions are built around the most advanced technologies that includes data mirroring and file syncing.
It has been said that the ultimate ransomware countermeasure is backup. Cloud based data backup solutions are built around the most advanced technologies that includes data mirroring and file syncing.
If the data on your machine is backed up and stored out of reach from hackers, ransomware is little more than nuisance. However, bad guys have started looking for ways to attack backup files! Leaving us nothing to combat ransomware!
Good thing there is Acronis Active Protection! The only backup software that can stop this kind of attack. A powerful stand against ransomware that helps protect your data from this nefarious, modern data threat. Safeguards your backup data from recent ransomware like Petya, WannaCry and Osiris.
Cyber attacks will continue to occur daily and security incidents becoming more costly. So companies need to invest in a SOC in order to avoid heavy loss to the company and to help improve their security operations proficiency, efficacy, and quality, in order to keep their cyber incident under control.
A SOC gives an organization the ability to anticipate and respond more quickly to threats, work more collaboratively and share knowledge more effectively. But it requires a commitment and accountability, highly skilled individuals and much advanced tools needed. Without it, the SOC can never realize its full potential.
Follow us on Linkedin
Subscribe to our monthly newsletter
